The United States Coast Guard (USCG) has a strong tradition of collaborating with owners and operators in the Marine Environment (ME) to provide relevant information about best practices to secure their critical systems.
Since December 2020, Coast Guard Cyber Command (CGCYBER) has vastly grown its presence and increased its operational tempo to protect cyber systems underpinning the ME. The observations and findings in this report provide Coast Guard units and their port partners with relevant information to identify and address cyber risks.
Coast Guard Cyber Protection Teams (CPTs) and the Maritime Cyber Readiness Branch (MCRB) developed these findings through technical engagements throughout 2022 with ME partners.
KEY TAKEAWAYS
- CGCYBER identified similar cybersecurity deficiencies at new organizations assessed in 2022 commensurate with our 2021 CTIME Report recommendations. 2022 CPT missions reinforced many of the same recommendations to ME organizations provided to other organizations in 2021 related to basic cyber hygiene, including implementing a Patch Management Policy, enforcing the principle of Least Privilege, and implementing a Strong Password Policy, or Multi-Factor Authentication (MFA).
- Emerging technologies introduce new attack vectors to the ME. There is a rapid increase in the use of cloud-based environments and remote-access solutions for ME networks. These new technologies bring many benefits; however, they introduce risks if not implemented correctly. These risks become even more significant when cloud environments are bolted onto legacy systems or services without adequate security controls. It is essential for organizations to understand the risks of new technology and the available safeguards to mitigate those risks.
- Opportunistic Cyber Criminals and Advanced Persistent Threats (APTs) continue to target the ME. Cyber criminals continue to profit from disruption of critical functions and often gain access by targeting company users with methods such as Phishing for Information or by Compromising Systems with Known Exploitable Vulnerabilities (KEV). APTs are more focused and use a variety of tactics, ranging from exploitation of common vulnerabilities to installation of sophisticated malware. The Cybersecurity and Infrastructure Security Agency (CISA)/CGCYBER Joint Alert AA22-174A provides a sample of techniques discovered by CGCYBER believed to be used by APTs.
- Importance of Timely Information Sharing: Timely information sharing is the most effective universal action to strengthen the ME, prevent future cyber-attacks, and enable timely response to exploitable vulnerabilities. CGCYBER observed a promising increase in voluntary reporting in 2022, but many organizations remain reluctant to report or share information with the Coast Guard or other partners. The Coast Guard continues to encourage information sharing through Department of Homeland Security (DHS)-sponsored public-private partnership groups, like Area Maritime Security Committees (AMSCs) or the Maritime Transportation System Information Sharing and Analysis Center (MTS-ISAC). These groups can facilitate this information sharing, while addressing the organization’s privacy concerns.
UNDERSTANDING THE MARINE ENVIRONMENT
The ME consists of 25,000 miles of coastal and inland waterways, serving 361 ports, 124 shipyards, more than 3,700 maritime facilities, 20,000 bridges, 50,000 Federal aids to navigation, and 95,000 miles of shoreline that interconnect with critical highways, railways, airports, and pipelines, as well as undersea cables carrying 99% of U.S. communications abroad. Approximately $5.4 trillion flows through the ME annually, constituting 25% of the United States gross domestic product; 90% of U.S. imports and exports enter or exit by ship. The ME is one of the most crucial elements of the global supply chain.
During the height of the COVID-19 pandemic, shipping bottlenecks at various U.S. ports, most notably Los Angeles/Long Beach, led to significant delays and rising costs. With transit times from China to Los Angeles, including the time waiting for an open berth, nearly doubling, retailers incurred approximately $321 million in added interest due to port congestion. This is in addition to the approximate quintuple increase in costs to ship a container due to the increased demand.
Figure 1: Critical Infrastructure Sectors with ME Organizations
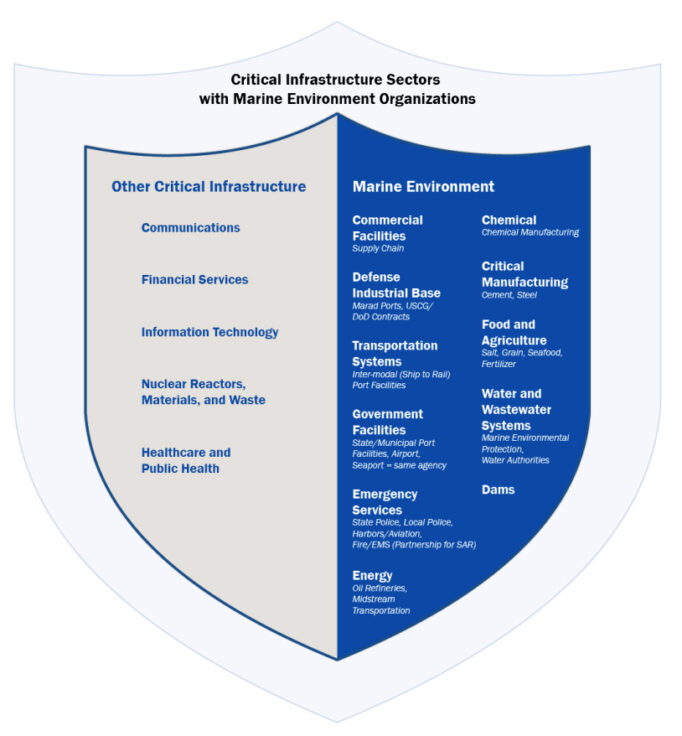
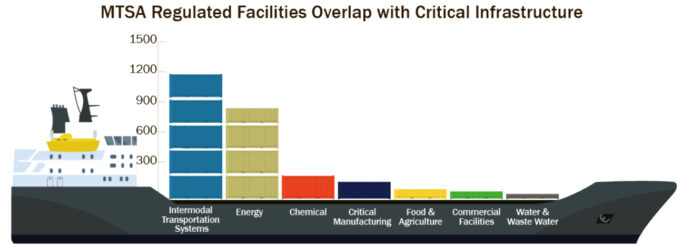
The ME is comprised of more than ships, ports, shipyards, and other related infrastructure. Of the more than 3,700 waterfront facilities, more than half overlap with at least one other Critical Infrastructure Sector. Regulated Facilities and Critical Infrastructure Sectors provides a depiction of Coast Guard regulated facilities and what other Critical Infrastructure Sector(s) they represent.
Figure 2: Overlap Between MTSA Regulated Facilities and Critical Infrastructure Sectors
MARITIME CYBER TRENDS
In 2022, MCRB and local Coast Guard units investigated 59 cybersecurity reports including phishing/spoofing, ransomware attacks, and other cyber incidents. This included several largescale incidents affecting multiple organizations at once. With more than $5.4 trillion and 90% of U.S. imports and exports flowing through the ME annually, nation state actors wishing to harm the U.S. and opportunistic cyber-criminal and ransomware gangs, consistently target the ME.
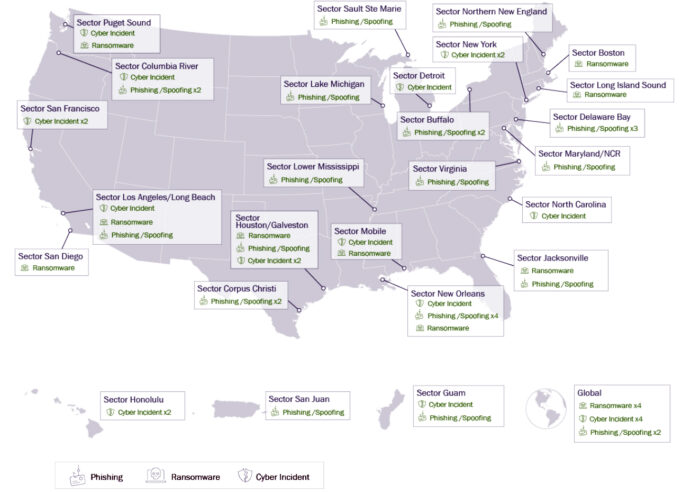
Cyber Command Spear-phishing campaigns continue to proliferate across the ME. Malicious cyber actors (MCA) use techniques ranging from typo-squatted domains to account/business email compromises. These campaigns are often able to deliver malware, resulting in MCAs extorting entities within the ME for financial gain. CGCYBER’s observations are bolstered by public reporting of similar campaigns targeting3 and impersonating major shipping entities. Ransomware remains a popular end game for 13 criminal gangs targeting maritime entities around the globe; the Lockbit ransomware attack against the Port of Lisbon is a prime example. Figure 4 provides a visual of the investigated cybersecurity reports.
Figure 4: 2022 Cyber Events Reported to Coast Guard
Furthermore, in 2022, criminals were observed targeting back-up systems to make recovery more difficult and to increase pressure on the executive decision makers to pay the ransoms. In addition to financial extortion, these incidents often result in months of reduced operational capacity and potential reputational impacts.
Maritime shipping companies continue to be the target of all types of cyber criminals, but in 2022, CGCYBER also observed a significant increase in malicious cyber actors targeting liquified natural gas processors/distributors, and petrochemical companies. These efforts included increased reconnaissance, scanning, sophisticated spear-phishing campaigns, and ransomware. The ALPHV ransomware attack against a maritime-based oil company provides an example of the operation-crippling malware that MCAs employ.
In this example, 13 facilities were unable to transfer onload or offload fuel causing economic disruption. Additionally, CGCYBER observed several significant cyber-attacks targeting maritime logistics integrators and technology service providers. These include the ransomware attack that shutdown operations for logistics company, and a separate attack impacting more than 1,000 customers of a maritime technology provider. These types of attacks are particularly concerning due to the extent of the second order impacts in the ME. Because they are integral elements of the supply chain, many other maritime organizations were affected concurrently.
Timely information sharing amongst other government agencies (OGAs), CGCYBER, and ME organizations continued to be key to identifying and disrupting MCA operations. For example, CGCYBER notified a facility of a Known Exploitable Vulnerabilities (KEV) on their network exposed to the public Internet. The subsequent Coast Guard CPT engagement with this organization resulted in the detection and removal of an MCA from the partner’s network (reference Joint Alert AA22-174A, Appendix C: Maritime Cyber Alerts). Further, timely information sharing with Cybersecurity and Infrastructure Security Agency (CISA), led to detection of additional compromises by the same MCA within the U.S. Critical Infrastructure.
As the Coast Guard continues to combat wrongful actions by MCAs, CGCYBER relies on cyber incident reports to the National Response Center (NRC) to activate response capabilities and increase awareness across the ME. The Coast Guard urges organizations in the ME to report all cyber incidents to the NRC. Through free-flowing multi-directional information sharing in the ME, the Coast Guard and ME organizations can best address these evolving cyber threats.
FINDINGS
In a CY21 & CY22 Comparison, Marine Transportation System (MTS) partners Fully or Partially Mitigated 93% of all findings within six-months of receiving a CPT Assess mission, an 11% increase from 2021. Other than a slight decrease in Partially Mitigated findings, which is believed to be a result of the increase in Fully Mitigated, all remediation efforts improved from 2021 to 2022. These metrics validate the conclusion that organizations in the ME can take quick and effective action to reduce their attack surface, particularly if they understand the business impacts associated with the risks.
Phishing for Information Phishing for Information is a sub-technique of the Phishing Technique. Phishing for Information is categorized as a reconnaissance technique by the MITRE Corporation rather than an initial access technique. Instead of attempting to use the email for malicious code execution, Phishing for Information is used to gain useful information, such as a username and password, from the phished user. During Coast Guard CPT missions, 9.3% of all phishing emails sent during threat emulation resulted in a click by a user. Additionally, of those users who clicked the link, 76.4% of users provided credentials when requested. Due to the unpredictability of a specific user acting after receiving a phishing email, this technique may be more successful for non-targeted phishing campaign compared to a spear-phishing campaign targeting specific users. According to IBM Security’s “Cost of a Data Breach Report 2022,” compromised credentials were the most common cause for data breaches. When MCAs employed Phishing for Information, it took organizations an average of 327 days to detect (longest time to identify compared to other vectors) and had the average highest cost per data breach at $4.83 million, excluding ransom payments. This data reinforces the severity of the most common finding detected by Coast Guard CPTs.
Related Mitigations:
- Common Mitigation #6: User Training
- Software Configuration (configure Sender Policy Framework (SPF)/Domain Keys Identified Mail (DKIM)/Domain-based Message Authentication Reporting and Conformance (DKIM) for mail server).
Valid Accounts. The most common initial access technique used during Assess missions was Valid Accounts. Valid Accounts were often gathered from publicly available sources or from using related techniques such as Phishing for Information, Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay, or Steal or Forge Kerberos Tickets: Kerberoasting. Coast Guard CPTs gained initial access to the target networks using gathered account information.
Related Mitigations:
- Common Mitigation #1: Password Policies
- Common Mitigation #4: Privileged Account Management
- Common Mitigation #6: User Training
- Common Mitigation #7: User Account Management
- Application Developer Guidance
Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning & SMB Relay. LLMNR/NBT-NS Poisoning and SMB Relay attacks leverage antiquated features used for host identification to harvest credentials from within a network. LLMNR/NBT-NS Poisoning consists of an attacker inside the network responding to LLMNR (UDP 5355)/NBT-NS (UDP 137) and directing traffic to an adversary-controlled system. Then, once the requestor attempts to access the adversary-controlled system, the adversary can use a myriad of techniques to directly obtain hashed or even sometimes plaintext credentials. If the adversary captures a password hash, they can pivot to the Brute Force: Password Cracking technique to determine plaintext credentials.
Related Mitigations:
- Common Mitigation #3: Filter Network Traffic
- Network Segmentation
- Network Intrusion Prevention
- Disable or Remove Feature or Program
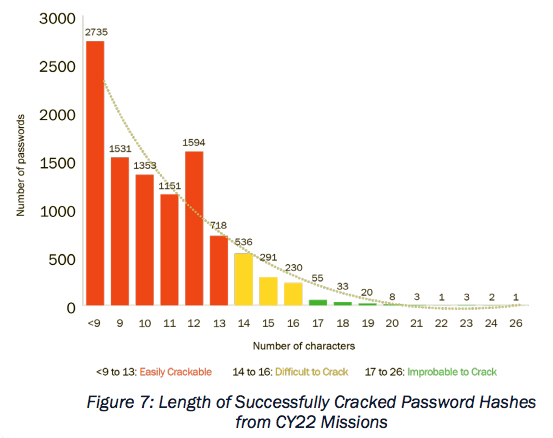
Brute Force: Password Cracking. A weak password policy can result in an attacker gaining unauthorized access to a system or application. According to the National Institute of Standards and Technology (NIST) Special Publication 800- 63 Digital Identity Guidelines, a strong password policy includes password length and password complexity. It also contains suggestions for enforcement and consequences when not followed (lost system access). A good password policy can protect an organization from brute force password cracking, guessing, and reuse. Figure 7 illustrates the number of successfully cracked hashes across the length of the password from CPT missions. As can be seen, the longer the password, the more difficult the hash is to crack. For over 17,000 discovered password hashes, CPTs were able to crack hashes for 60.1% of all passwords using hybrid dictionary and ruleset-based password cracking. The median password length of all cracked passwords was ten characters. CPTs were unable to determine the length of any password that was unsuccessfully cracked. CPTs were able to pre-calculate and successfully crack the hashes for all passwords less than eight characters in length. Of the cracked passwords, 97.1% of passwords had at least three complexity requirements (uppercase letter, lowercase letter, number, symbol) showing that most users implement these requirements into their passwords in predicable ways without increasing the overall difficulty to crack the password. Our Assess missions validate NIST’s recommendation that password length is the primary factor in characterizing password strength. Our ruleset-based password cracking was able to detect most complexity techniques used in user-created passwords. Only 198 recovered passwords were seven characters or less. This is attributed to compliance with NIST’s minimum password recommendation of eight characters or more. However, in comparison to the NIST standard, the U.S. Department of Defense (DOD) requires a minimum 15-character password length for all accounts when the user or app cannot support multi-factor authentication.
Related Mitigations:
- Common Mitigation #1: Password Policies
- Common Mitigation #2: Multi-Factor Authentication.
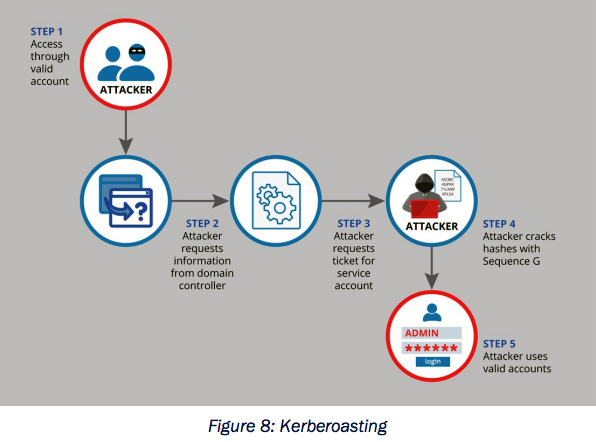
Steal or Forge Kerberos Tickets: Kerberoasting. Applications often require user accounts to operate, known as Service Accounts. Service Accounts use elevated privileges to perform a business function. MCAs leverage techniques such as “AS-REP Roasting” (related to Authentication Server Requests) and Kerberoasting to abuse legitimate functionality and attain a copy of the Service Account’s password hash. If the service account has a weak password, the MCA can crack this password using the Brute Force: Password Cracking technique and access systems using the Service Account credentials. Figure 8: Kerberoasting illustrates the basic process flow of a Kerberoasting attack. For simplicity, administrators often use existing administrator accounts as Service Accounts or create a new account and add the new Service Account to an existing administrator group, such as Domain Administrators. This allows MCAs to leverage these unnecessary permissions to gain full control over an enterprise.
Related Mitigations:
- Common Mitigation #1: Password Policies
- Common Mitigation #4: Privileged Account Management
- Encrypt Sensitive Information (Enable AES Kerberos).
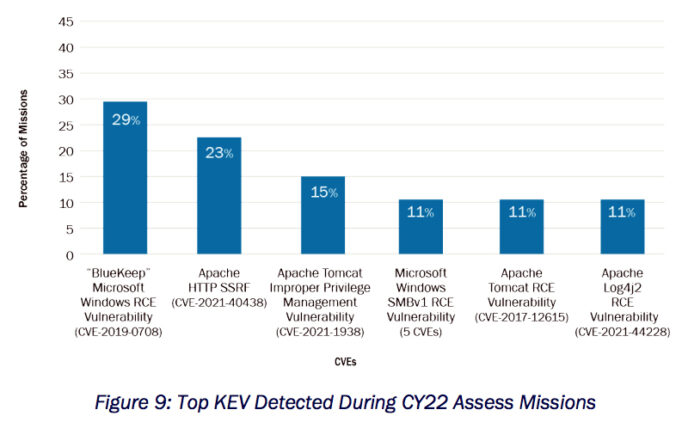
Patch Management. Vendors release patches and updates to address existing and emerging security threats and address multiple levels of criticality. Failure to apply the latest patches can leave the system open to attack from publicly available exploits. The risk presented by missing patches and updates can vary; however, the most critical of vulnerabilities are those that are proven exploitable. These vulnerabilities are listed in CISA’s KEV Catalog. Figure 9 represents the vulnerabilities from the KEV Catalog detected during CPT Assess missions. In addition to the presence of KEVs in these networks, CPTs regularly observed a lack of network filtering (see Mitigation #3: Filter Network Traffic) or network segmentation. These security architecture concerns show that if an adversary could exploit a vulnerability at one of these sub-organizations, they could easily pivot into and throughout the internal environment of the organization. Appendix G: Known Exploitable Vulnerabilities Detected on CPT Missions contains descriptions of these vulnerabilities.
Related Mitigations:
- Common Mitigation #4: Privileged Account Management
- Common Mitigation #5: Update Software
- Application Isolation and Sandboxing
- Disable or Remove Feature or Program
- Execution Prevention
- Exploit Protection
- Network Segmentation
- Threat Intelligence Program
- Vulnerability Scanning.
For more details on mitigations and appendices, you may download the full report.
